Protect clients’ sensitive data — prevent data leakage from workloads via peripheral devices and network communications by analyzing the content and context of data transfers and enforcing policy-based preventive controls.
No need to drill down into client business details and define policies manually. Automatically baseline and profile sensitive data flows to create and continuously adjust DLP policies to ever-changing business specifics, ensuring protection against the most common causes of data leaks.
Enable rapid response and forensic investigations and simplify DLP policy maintenance via centralized audit logs and alerts on security events. Ease reporting with information-rich widgets.
We offer you to get your FREE trial in partnership with Acronis.
Simply fill the form, and get your Trial immediately.

Leverage pre-built data classifiers for most common regulatory frameworks protecting personally identifiable information (PII), patient health information (PHI), cardholder data, and documents marked as confidential.


Improve your revenue per client and attract more clients with high-demand, MSP-managed DLP services that are easily accessible for clients of all sizes.
Control your TCO and enable better margins with easier service tiering by using a single, integrated platform for backup and disaster recovery, next-generation anti-malware, email security, workload management and data loss prevention.
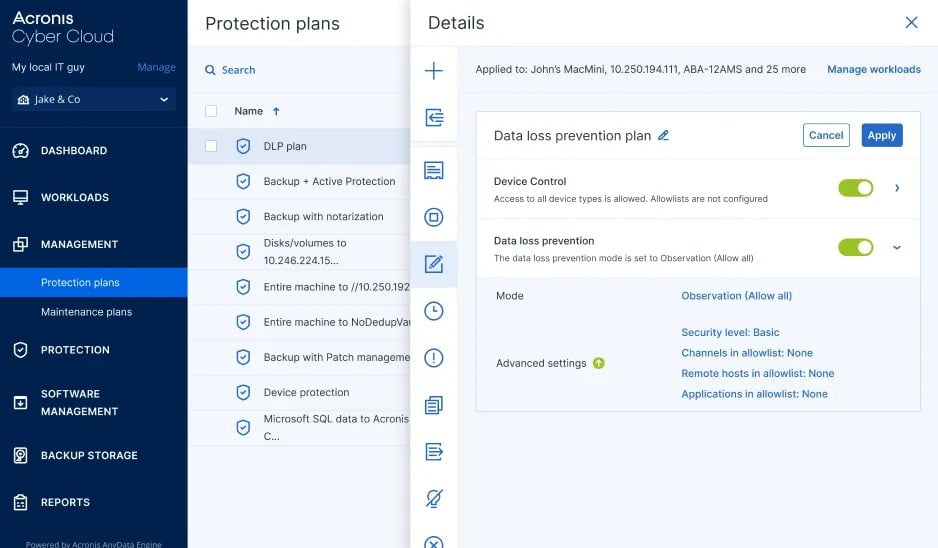


Minimize manual work and the risk of error. Simplify provisioning by automatically creating an initial DLP policy for each client with a behavior-based approach.
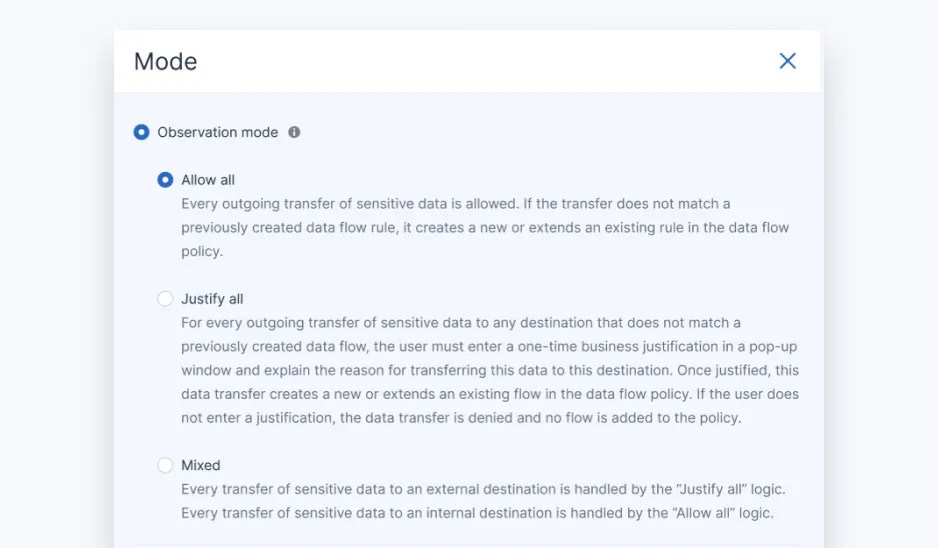
Baseline and profile outgoing sensitive data flows across organizations to automatically map clients’ business processes to a DLP policy — adjusted to their specifics. Leverage optional end-user assistance for higher accuracy, and request client validation before enforcing a policy.
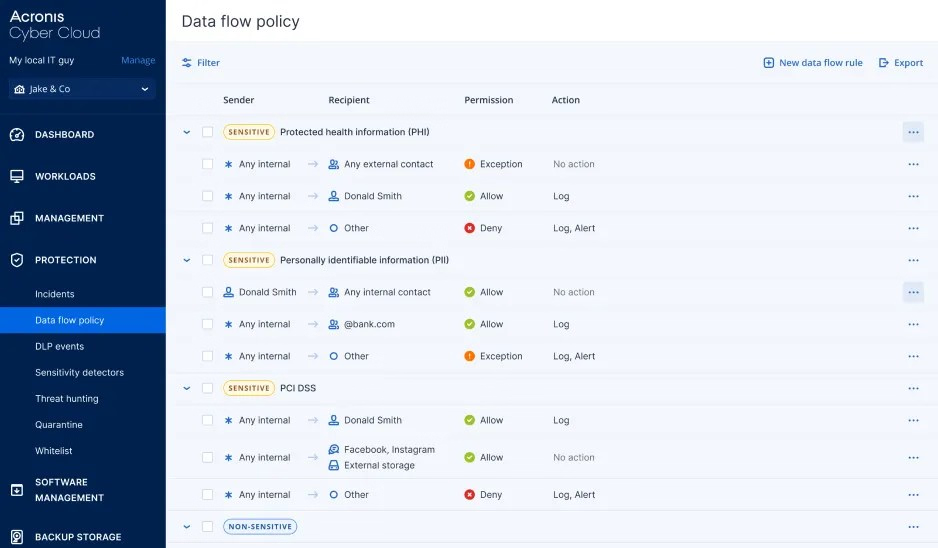
Control data flows across most common local and network channels, including removable storage, printers, redirected mapped drives and clipboard, emails and webmails, instant messengers, file sharing services, social networks, web access, and network protocols.
Ensure web-browser-independent control of data transfers to social media, webmail and file-sharing services. Leverage content inspection of outgoing instant messages and sensitive data detection in images sent from remote and offline computers.
Control your TCO, reduce management overhead and boost margins by using a single solution that integrates backup, disaster recovery, next-generation anti-malware, email security, workload management, and data loss prevention.

Tech Fortress is a leading company in cybersecurity and information technology, offering comprehensive solutions designed to protect your business from threats and enhance your IT infrastructure.
Copyright Tech Fortress © 2024 All Right Revered.