Block email threats, including spam, phishing, business email compromise (BEC), account takeover (ATO), malware, advanced persistent threats (APTs), and zero-days before they reach end users’ mailboxes. Leverage this next-generation, cloud-based email security solution for holistic protection.
Minimize email risk for clients with powerful threat intelligence, signature-based detection, URL reputation checks, unique image-recognition algorithms, and machine learning with DMARC record checks.
Detect hidden malicious content by recursively unpacking embedded files and URLs and separately analyzing them with dynamic and static detection engines.
Prevent advanced email threats that evade conventional defenses with a unique CPU-level technology able to act earlier in the attack chain to block exploits before malware is released, delivering a clear verdict within seconds.
We offer you to get your FREE trial in partnership with Acronis.
Simply fill the form, and get your Trial immediately.


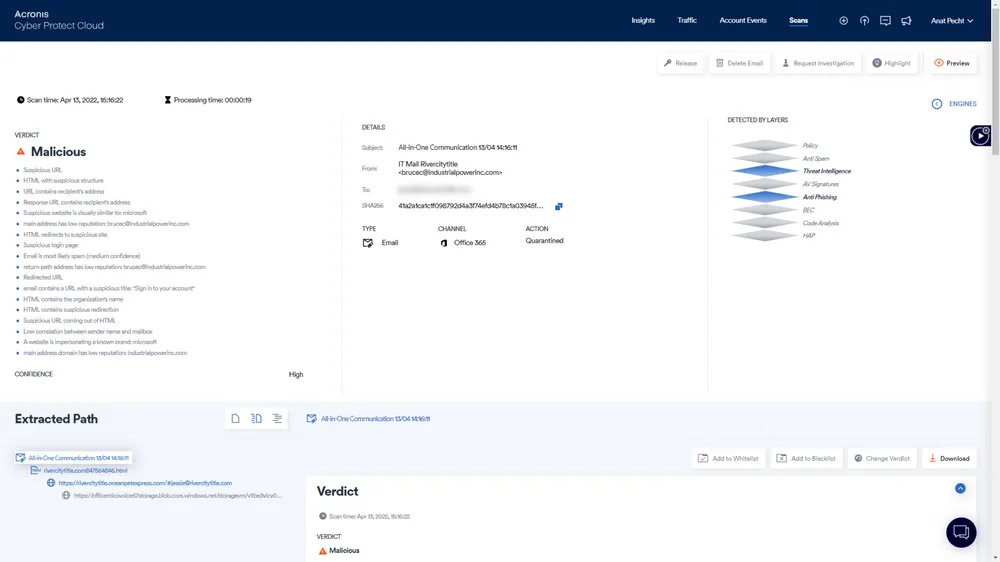
Replace the inefficient security stack of sandboxes and content disarm and reconstruction technologies (CDRs) with a multi-layered email security solution for lightning-fast detection that’s easy to deploy and manage.
Protect clients’ collaboration apps, increasingly exploited in attacks with prioritized patching and exploit prevention. Leverage Acronis Cyber Protect Cloud, integrating backup and disaster recovery, next-generation anti-malware, and cyber protection management.
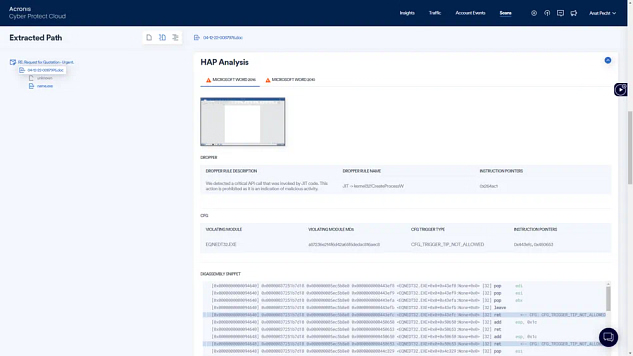
Perform DR testing in an isolated environment to confirm application availability, ensure compliance, and prove DR readiness — without any impact on production systems.
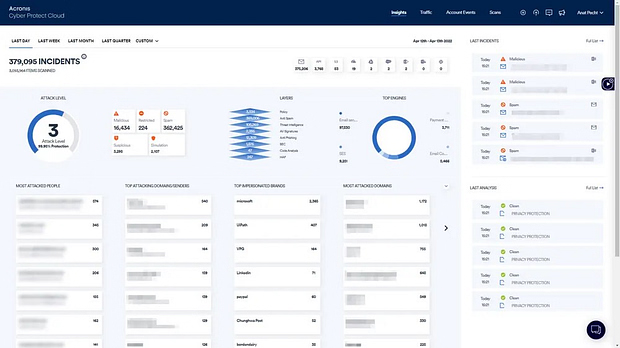
Leverage a holistic view of the threat landscape across organizations with forensics data for each client and email, proactive insights on threats a targeting clients and most risky attack patterns, and analysis of any file or URL on which your team needs forensics.
Gain direct access to cyber analysts that act as an extension of your service delivery team, monitor all customer traffic, and analyzing malicious intents with ongoing reporting and 24/7 support, including handling false positives, remediating, and releasing as required.

Tech Fortress is a leading company in cybersecurity and information technology, offering comprehensive solutions designed to protect your business from threats and enhance your IT infrastructure.
Copyright Tech Fortress © 2024 All Right Revered.